Keeper Writeup — HTB
Hello everyone! This is my first writeup for a HackTheBox’s machine. Hope you enjoy! If you have any tips or want to comment something about this writeup (or something I could have done better), please do! Thanks in advance!
I’m using Parrot 5.3 Security Edition for this writeup.
First, I’ll start checking the top 1000 open ports (since it’s an easy machine, shouldn’t be that hard to get an open port for exploiting). I like to use -vv just for checking more info while scan is being done.
nmap -sC -sV -vv [MACHINE IP]
Apparently we have a nginx 1.18.0 running. Let’s check the website’s content.

As some other machines, we’ll need to add the hostname to our /etc/hosts file.
sudo nano /etc/hosts
Ok, after adding the hosts and clicking the link, we get to another page.

Trying “admin/admin” and “admin/password” didn’t work. Let’s search the RT’s default username and password for checking if it works.
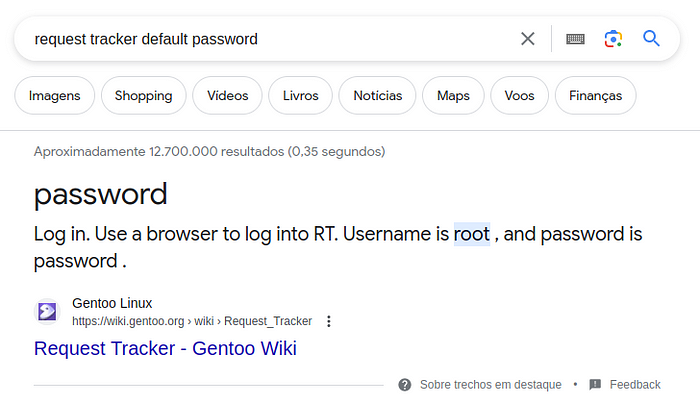
Magically it worked. Now we’re inside the Request Tracker.

I’ll try to search the tickets for any clue.


We’ve found a ticket from Enoch Root to Lise Nørgaard.

Nothing really useful, but now we know there’s two users in this system.
Let’s head to the Users area.


Let’s check both users for more information.


Next step is test if this credentials are working, maybe user ‘lnorgaard’ uses the same password for the machine.
ssh lnorgaard@keeper.htb
## password Welcome2023!

Now, we’re heading to the root flag. I like to user two commands to check SUID and Sudo permissions.
sudo -l
find / -perm -u=s -type f 2>/dev/null

Noticed there’s a file named “RT30000.zip” inside. We’ll open a quick HTTP server using Python to get this file and check its content.
python3 -m http.server
On our side, we’ll download the file and check what’s inside.
wget http://[MACHINE IP]:8000/RT30000.zip

We have two files inside, a .dmp file and a .kdbx file. After some search, it seems that “KeePassDumpFull.dmp” is a dump file from Windows’ KeePass software, and “passcodes.kdbx” is a KeePass file for some kind of password (maybe root password).
There’s a CVE for KeePass dump files (CVE-2023–32784), and there’s a GitHub PoC for this specific scenario (check here).
I’ve downloaded the same files on my Windows for better checking, GPU stuff and all. After cloning the repo, let’s try to check the .dmp content if the CVE works.
dotnet run [Path to dump]
So, we get the following “probable” pasword (considering * as a wildcard character, since the PoC wasn’t able to retrieve from file):
*{l, `, -, ', ], A, I, :, =, _, c, M}dgr*d med fl*deEssentially, we know the PoC file couldn’t retrieve three characters, considering the first one will always be a wildcard. So we have “**dgr*d med fl*de”. Considering the username “lnorgaard” and the user being “Lise Nørgaard”, after a Google search for this last name, we see that this is usually a Dannish lastname.

So, what if we just pasted our password in Google Translate to check if something pops up?

What happens if we tried to remove the asterisks?

That would probably be the password, let’s check it downloading and using KeePass to open the “passwords.kdbx” file.


Double clicking “keeper.htb” entry, we get some interesting info.

Couldn’t be that easy, huh? If permission for login is denied using password, I guess there’s other way around it. When you double-click “keeper.htb” entry, you’ll see that the notes are interesting.

Next step we’ll copy this text and save it on a “file.ppk”, then try to open with PuTTYGen.

Next, we’ll go on Conversions > Export OpenSSH key (force new file format), and save as “key.pem”. Then, we’ll use this key to try SSH again on keeper.htb to see if it works.
ssh -i key.pem root@keeper.htb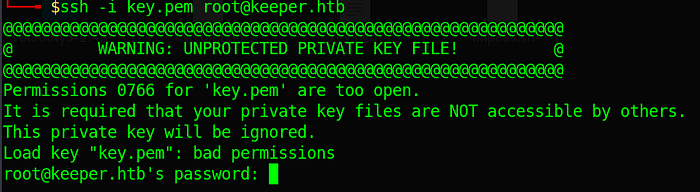
Apparently that your private key can’t be accessible by others, so let’s reduce the permissions and try again.
chmod 700 key.pem
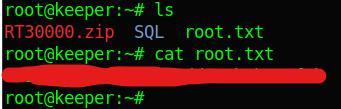
Last step, same as user flag, check if the flag is on “/root”, then get the flag.
Hope you enjoyed it, thanks for reading it!





